ニュース
本記事ではコードインジェクション攻撃に関する論文を紹介します。
この攻撃には SQL Injection や XSS などの手法が含まれ、サイバー攻撃として最も定番の攻撃と言えます。
これらの攻撃は近年たびたび話題に上がる情報漏洩を引き起こす原因となっており、これを防ぐことはサイバーセキュリティクラウドの理念
"安心安全なサイバー空間を創造する" というミッションの実現において極めて重要な課題となります。
本記事ではこの悪名高い攻撃を AI によって補足する際に役立つ知見をご紹介できればと思います。
尚、この記事は以前出したものの日本語版です。英語で読んだほうがわかりやすいという方はこちらをお読みください。
Note that this article is the translated edition of the previous issue. You can read the same contents of this article in English. If you need it, please go to the following article.
[Introduce Paper] CODDLE: Code Injection Detection With Deep Learning
概要
本記事では CODDLE: Code-Injection Detection With Deep Learning が提唱する、コードインジェクション攻撃を機械学習によって検知させるうえで役立つ知見を紹介します。CODDLE の提案する手法は主にデータの前処理に関するもので、著者曰くこの手法を用いることで検知精度が向上したそうです。
提案手法
提案手法の鍵となるポイントは「いかにして入力データを機械学習にとって理解しやすいものに変換するか?」という命題。これを実現するために、ノイズの除去 および 記号化 という2つの手法を用います。
ノイズの除去
ここでいう ノイズ とは、AI がパターンを学習するさいに障害となる要素のことです。例としては各種トークンや UUID のほうなランダム文字列、タイムスタンプのような数値、ファイル名といったものが挙げられます。例えば機械学習モデルで SQL Injection のパターンを学習させたいと考えたとき、モデルが注目すべきは SQL の構文、すなわち構造に関するパターンであり個々のカラム名や Value の値には注目して欲しくないわけです。もしもこのような要素を学習してしまうと、特定の Value が来たときにしか検知できない。というようなモデルになってしまいます。このように学習時に用いたデータに対してて適合しすぎために、未知のデータに対応できなくなる現象は 過学習 と言われ鮮度を落とす一因となります。
記号化
この手法のベースとなる主なコンセプトは、理想的なモデルは特定の演算子や記号の役割を理解している という考えに基いています。ではこれをどうやって実現するか?提案手法では AND, SELECT といった SQL 特有の予約語や、=, ) といった演算子および ‘ のようは記号を数値のコードに置換します。
ここで、符号化の手法として 単一 の値ではなく ペア の値を用いるというところも本論文独自の工夫が見られるところです。ペアとはすなわち、AND や SELECT といった個々のパターンを数値化したものに加え、それが属するカテゴリーに関するコードを追加で付与します。カテゴリーについては 予約語, 演算子, 記号 の3種類を用います。各カテゴリーとコードの対応は以下の通りです。
| Code | Category | Example |
|---|---|---|
| 0 | Operators | AND, UNION, SELECT, FROM |
| 1 | Expressions | =, ) |
| 2 | Escape Symbols | ` |
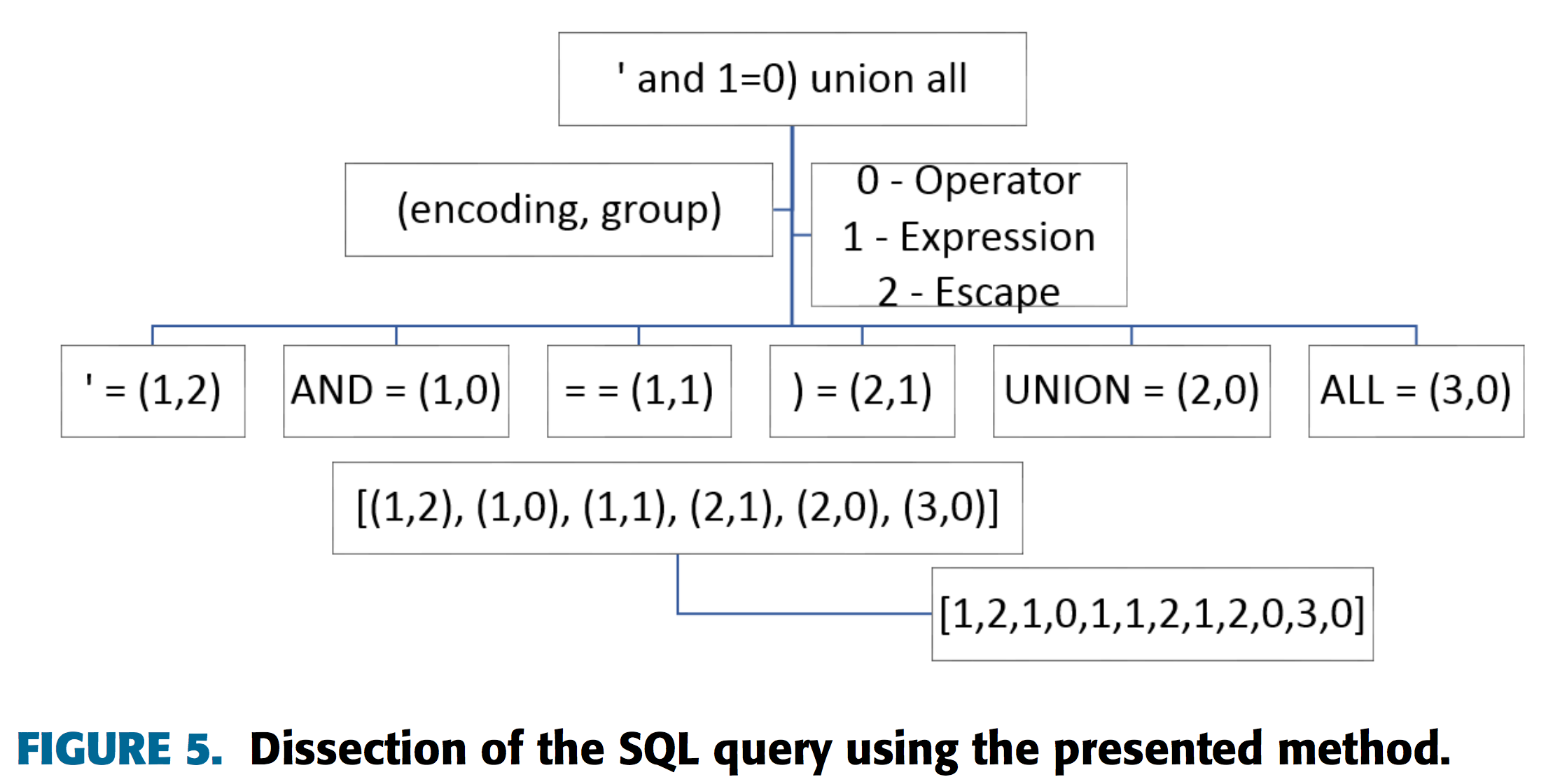
エンコードサンプル
ここでは、記号化 の節で解説した提案手法を用いたエンコーディングパターンの具体例を提示します。
SQL Injection
| Output | |
|---|---|
| Raw String | ` and 1=0) union all |
| Remove Randomness | ` and = ) union all |
| Encoding | (1,2),(1,0),(1,1),(2,1),(2,0),(3,0) |
| Output | |
|---|---|
| Raw String | SELECT column1, columns2, column3 FROM tablename |
| Remove Randomness | SELECT , , FROM |
| Encoding | (5,0),(3,1),(3,1),(10,0) |
XSS
| Output | |
|---|---|
| Raw String | <img src=1 href=1 onerror="javascript:" alert(1)"> |
| Remove Randomness | < img src = href = onerror = " javascript : " alert ( ) " > < / img > |
| Encoding | (1,0),(4,1),(4,1),(4,1),(5,0),(4,1),(2,1),(10,0),(3,1),(2,1),(3,1),(3,1),(6,1) |
評価
設定
論文では SQL Injection と XSS を対象に性能調査を行っています。機械学習の手法としては Convolutional Neural Network を、データには SQL/ XSS Payload Dataset を使用しています。
| Attack Type | Dataset | Data Source |
|---|---|---|
| SQL Injection | SQL Payload Dataset | https://github.com/SuperCowPowers/data_hacking/tree/master/sql_injection/data |
| XSS | XSS Payload Dataset | https://github.com/payloadbox/xss-payload-list |
結果
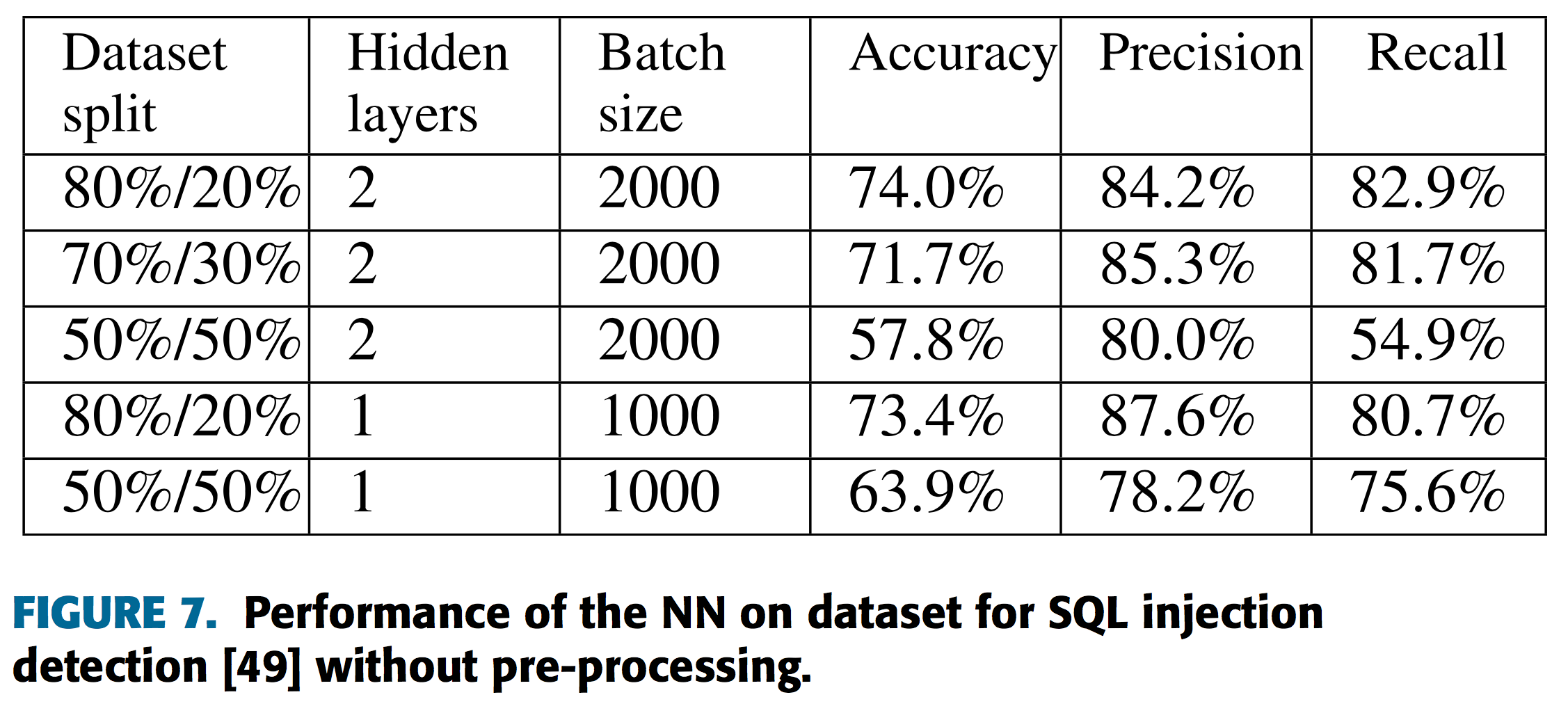
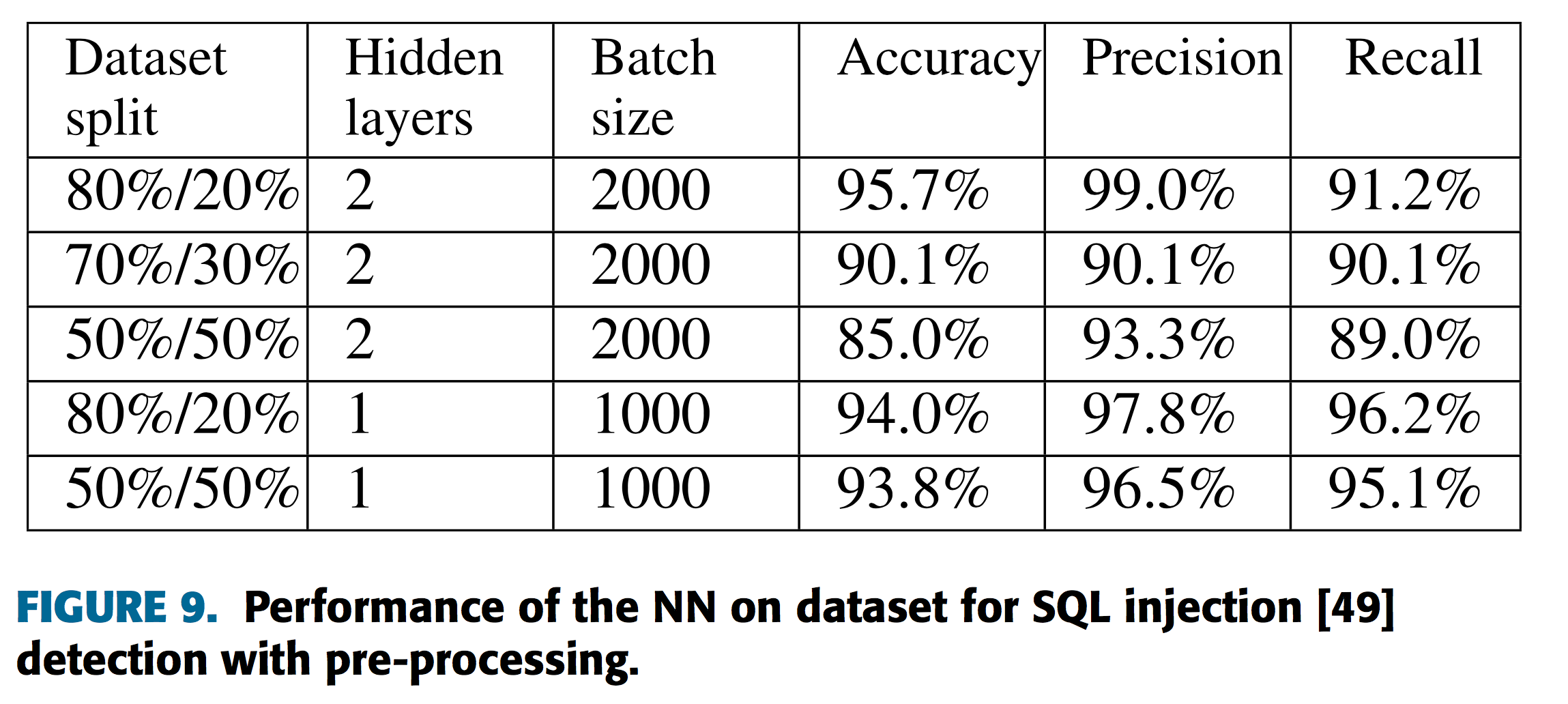
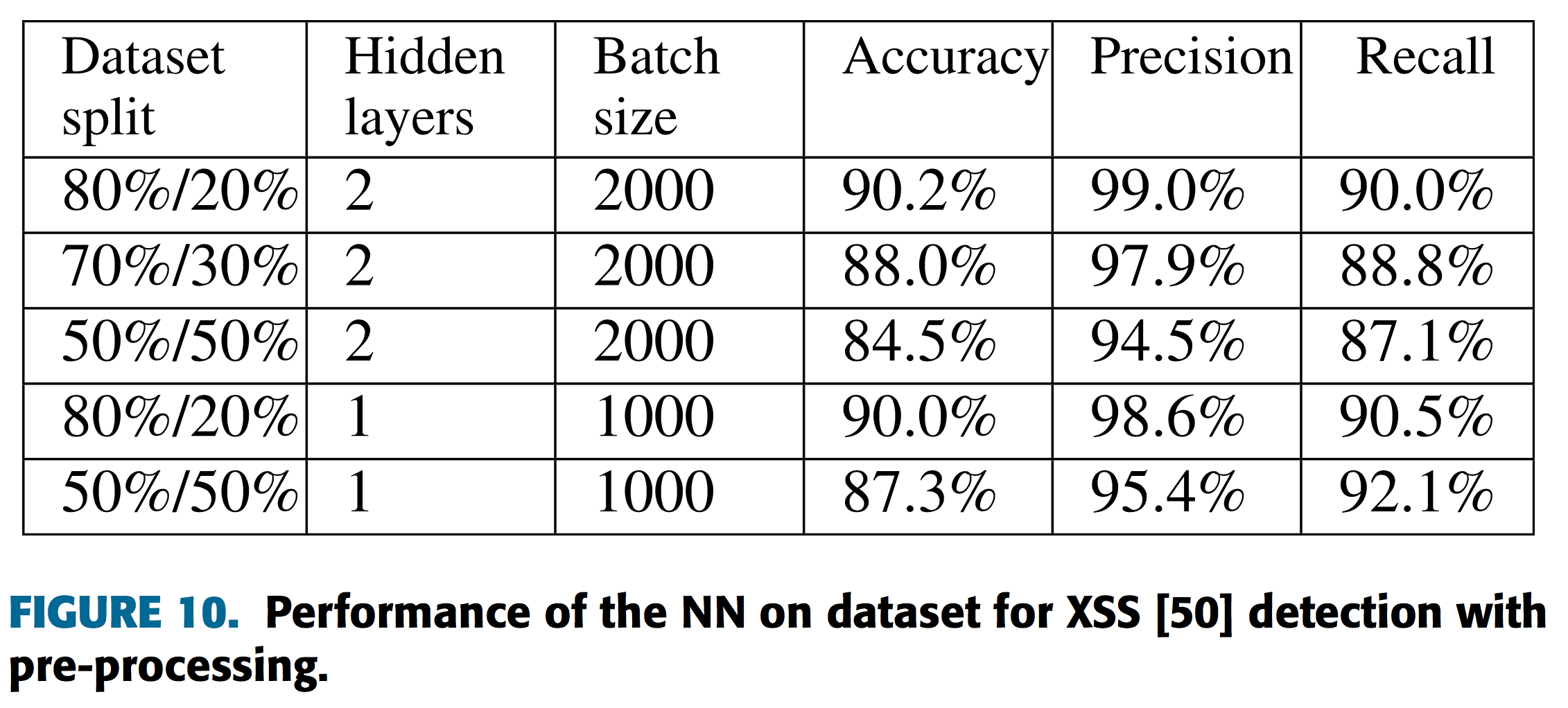
この結果から、提案手法を持ちることでより前処理を行わない場合と比較し優位な性能を実現していることがわかります。
コメント
検知精度の数値のみをみると結果は概ねいいように見えます。が、この提案手法にはいささか弱点もあるのではないかと考えられます。それは、以下の2点です。
- 部分文字列のコード化を行うためには言語ごとの予約語といったドメイン固有の知識が必要である
- 既知の表現にしか対応できない
このような制約から、対象とする言語に新規の関数が追加された場合などは、それが学習データに含まれないという状態が生じます。すると機械学習モデルはそのパターンを学習していないので、新規の関数を使用するような未知の攻撃には対応できないことになります。したがって、提案手法は既知の攻撃の検知においては役にたちそうですが、ゼロディ攻撃を始めとした新手の攻撃の検出を目的とする場合にはやや不都合があるかもしれません。しかしながら特定の文字列を符号化するというアプリーチや、入力データをAIに理解しやすい表現へ変換するといった根本にある考え方は参考になるところも多いのではないでしょうか。
参考文献
[1]CODDLE: Code-Injection Detection With Deep Learning
https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=8835902
[2][Introduce Paper] CODDLE: Code-Injection Detection With Deep Learning
https://www.cscloud.co.jp/news/tech/202004182545/
著者
佐々木 友輔
AI Researcher/ Product Developer
Cyber Security Cloud, Inc.
