News
- Press Release
Cyber Security Cloud adds new "SBOM management function" to vulnerability management tool "SIDfm VM"
Cyber Security Cloud, Inc. (Headquarters: Shinagawa-ku, Tokyo; President and CEO: Toshihiro Koike; hereinafter referred to as "the Company"), a global security manufacturer, is pleased to announce that it has added a new feature, "SBOM Management Function," to its vulnerability management tool, "SIDfm VM."

■ Development Background
In response to the increasing damage caused by cyber attacks exploiting weaknesses in the supply chain, various initiatives are being undertaken both globally and domestically. In the United States, a presidential order to strengthen cybersecurity was issued in May 2021, instructing the creation of a Software Bill of Materials (SBOM). In Japan, the Ministry of Economy, Trade and Industry published the "Guidelines for Implementing SBOM for Software Management" in July 2023. As a result of these efforts, many SBOM implementation support and generation tools have emerged, and the number of companies implementing SBOM is gradually increasing.
SBOM is used to increase the transparency of the supply chain, and is expected to be used particularly in the field of vulnerability management. There is an increasing need for software providers and users to realize effective vulnerability management by utilizing SBOM, including elements such as OSS (open source software) that constitute the software that they provide or use.
There are many SBOM implementation support and creation tools, and it has become relatively easy for software providers to deliver SBOM to users. However, to implement effective vulnerability management, it is necessary to quickly notice and appropriately deal with new vulnerabilities reported in OSS described in SBOM. Since the amount of software to be managed has increased compared to before the introduction of SBOM, there is an even greater demand for efficient collection of vulnerability information and decision-making on how to deal with it.
Furthermore, the process of dealing with issues is becoming more complex. For each product (and in some cases for each version) for which an SBOM is delivered, communication with the supply chain, management of the status of issues, and interim measures until the product can be updated are all required, requiring organizational efforts.
■ What is the new "SBOM management function"?
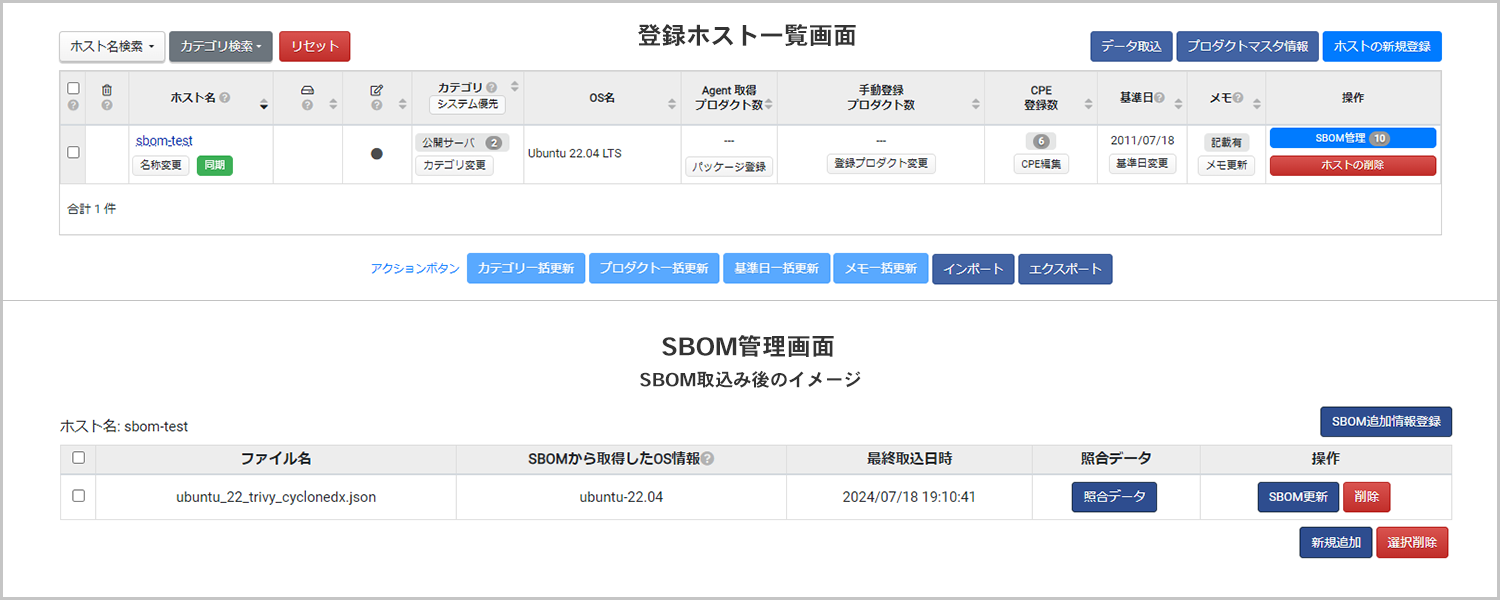
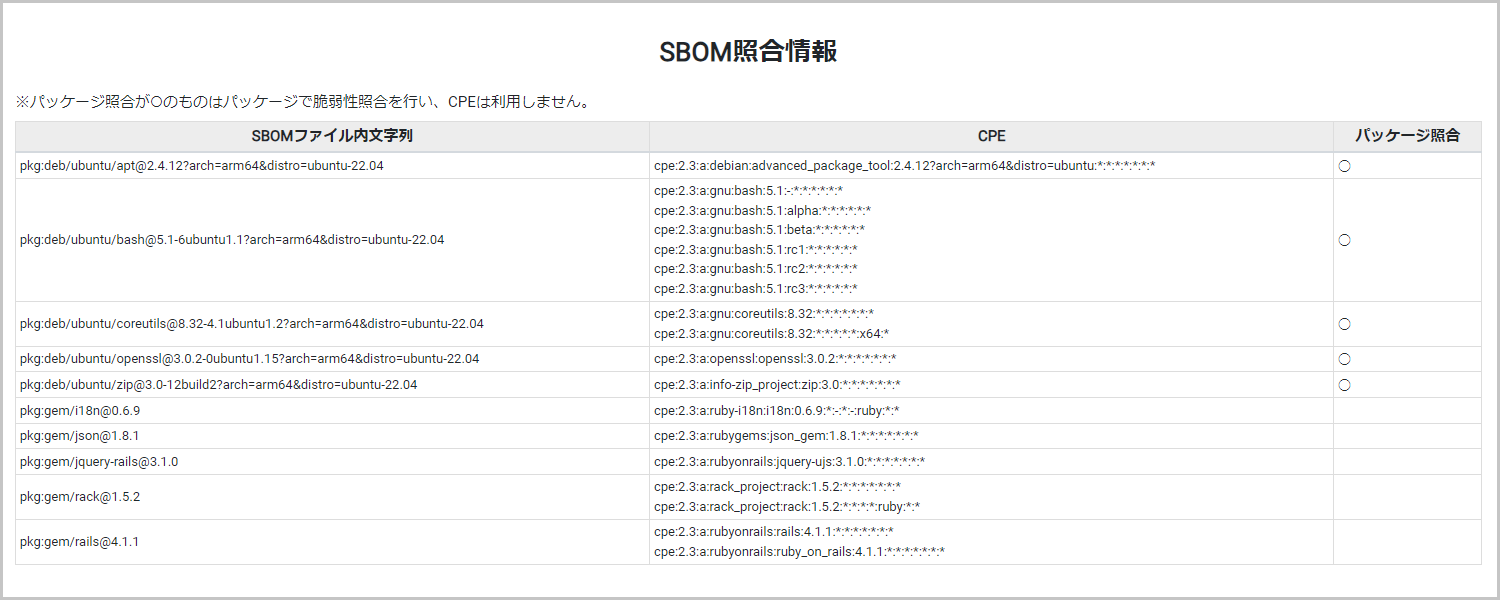
We have added a function to import SBOM files to SIDfm VM, which allows you to centralize vulnerability management. This allows you to check at a glance whether SBOM has been imported for each managed host by linking it with the host configuration information. In addition, imported SBOM can now be automatically converted into data for comparison with a vulnerability database, making it possible to detect vulnerabilities early.
Furthermore, by linking it as host configuration information, it is now possible to use SIDfm VM's custom category and rule setting functions to automatically share only the necessary information with the necessary personnel.
This allows security administrators to centrally grasp the status of each person in charge and the supply chain, along with vulnerabilities of hosts managed outside of SBOM.
・ SIDfm VM service site: https://sid-fm.com/vm/
*Currently, the following formats are supported. (There are two formats: json and xml.)
・SPDX: 2.2, 2.2.1, 2.2.2, 2.3, 2.3.1
・CycloneDX: 1.1, 1.2, 1.3, 1.4
■ Image of how to use the "SBOM management function"
As an example of how it can be used, we will introduce what can be achieved by using the "SBOM management function" from the perspectives of medical device manufacturers (MDM) and medical institutions (HCP) in the medical industry.
1: For medical device manufacturers (MDM): Compliance with basic requirements of the Pharmaceuticals and Medical Devices Act
・SBOM management (repository management) for each version of delivered equipment
・Detection and notification of vulnerabilities for each repository (automatic)
- Quickly understand the impact of detected vulnerabilities in Japanese and numerically (improving the efficiency of communication with delivery destination medical institutions and the supply chain, and reducing dependency on individual personnel)
2: For healthcare providers (HCPs)
・Check for vulnerabilities in the provided SBOM
・Understand the impact of detected vulnerabilities in Japanese and numerically
- Identify target devices that contain vulnerabilities
■About the vulnerability information collection and management tool "SIDfm"
SIDfm is a vulnerability information collection and management tool that streamlines vulnerability response operations. It automatically collects and accumulates vulnerability information for OS, applications, and network products from around the world. With a function that allows you to quickly identify only the information that is necessary for your company, you can see at a glance the vulnerabilities that need to be addressed and the details of the measures to be taken. In addition, it can even record and manage the progress of vulnerability countermeasures.
The biggest feature of "SIDfm" is the quality of its content. Security analysts interpret metadata from NVD, KEV, vendor advisory information, JVN, and other sources from an expert perspective, assess risk, and provide vulnerability information with "unique indicators" and "explanations in Japanese." With just the information from "SIDfm," you can immediately understand and grasp the affected versions and countermeasures in Japanese from the overview, allowing you to focus resources on addressing vulnerabilities that should be prioritized.

About Cyber Security Cloud, Inc.
Address: 13th floor, JR Tokyu Meguro Building, 3-1-1 Kami-Osaki, Shinagawa-ku, Tokyo
Representative: Toshihiro Koike Representative Director, President and CEO
Established: August 2010
URL: https://www.cscloud.co.jp/
With the corporate philosophy of "creating a cyberspace that people all over the world can use safely and securely," we are a Japanese security manufacturer that provides vulnerability information collection and management tools and fully managed security services for cloud environments, centered on web application security services that make full use of the world's leading cyber threat intelligence. As one of the global companies in cybersecurity, we will contribute to solving social issues related to cybersecurity and provide added value to society.
