社内セキュリティ
パソコンや社内ネットワークを守る
企業のサイバーセキュリティ対策は「社内セキュリティ」と「Webセキュリティ」に分けられます。
PCのウイルス対策やファイヤーウォールなどといった社内セキュリティと違い、Webサイトを守るためのセキュリティは対応できていないことが多く、近年は個人情報の漏えい事故が多数発生しています。
当社は、コストパフォーマンスが良くサポート体制も充実させたWebセキュリティサービスを追求しており、企業の規模やITスキルに関わらず利用できるよう日々品質を高めています。

パソコンや社内ネットワークを守る

誰もが訪れるWebサイトを守る

パブリッククラウドにて提供されているWAFを“AI”と“ビッグデータ”によって自動運用するサービス。
AWS Marketplaceから購入可能なAWS WAF専用のルールセット。世界で7社だけのAWS WAFマネージドルールセラーの1社として認定され、現在100以上の国と地域にサービスを展開。

AWSの各種セキュリティサービスを包括的に管理し運⽤するフルマネージドセキュリティサービス。

Webサイト・Webサーバへのサイバー攻撃を可視化・遮断する当社主力商品のクラウド型WAF。

パブリッククラウドにて提供されているWAFを“AI”と“ビッグデータ”によって自動運用するサービス。

AWSの各種セキュリティサービスを包括的に管理し運⽤するフルマネージドセキュリティサービス。
AWS Marketplaceから購入可能なAWS WAF専用のルールセット。世界で7社だけのAWS WAFマネージドルールセラーの1社として認定され、現在100以上の国と地域にサービスを展開。

OSやアプリケーションの脆弱性情報を世界中から収集し、リスクと併せて、パッチ情報や回避方法を日本語で提供するサービス。IT資産の脆弱性に対して決められた条件でチケット発行するなどの運用の自動化(SOAR)も可能。
Webアプリケーションやプラットフォーム、APIの脆弱性対策に関する脆弱性診断を包括的に実施。25年以上にわたる実績とノウハウをもとに、セキュリティ専門家&ツールによるハイブリッド診断を提供。

webtruでプライバシー対応を自動化。現状確認から分析、各規制対応が自動的に完了。面倒な手作業のチェックは必要ない。

Bunsin(ブンシン)で作成したメールアドレスを使っ個人情報を守る。迷惑メールをすぐにブロック、必要なメールだけが届く。
セキュリティとシステム開発による新しい価値を創造するテクノロジー企業。CSCのノウハウを元にクラウド構築やアプリケーション開発などを支援。

Web APIを保護するためのソフトウェアをOSSとして公開。APIゲートウェイのKongにセキュリティ機能を追加するプラグイン。
サイバーセキュリティクラウドは最先端のAI技術の開発や、世界トップレベルの脅威インテリジェンスの活用により、日々進化し続けるサイバー攻撃に対応します。
ディープラーニング(深層学習)を用いた攻撃検知AIエンジンCyneuralは、Webアクセスや多くの攻撃手法の研究で培ってきた知見を活用した特徴抽出エンジンを用いています。エンジンにおける複数種類の学習モデルを構築することで、一般的な攻撃の検知はもちろん、未知の攻撃の発見、誤検知の発見を高速に行います。
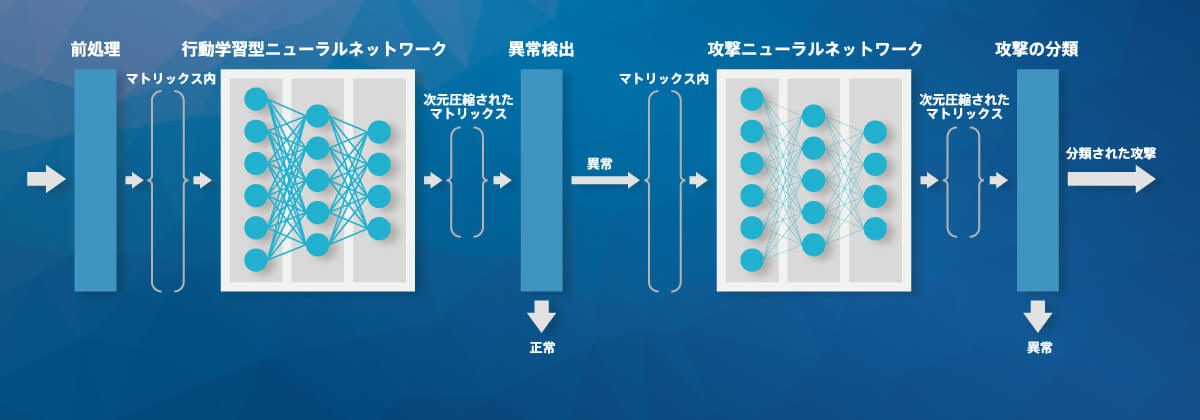
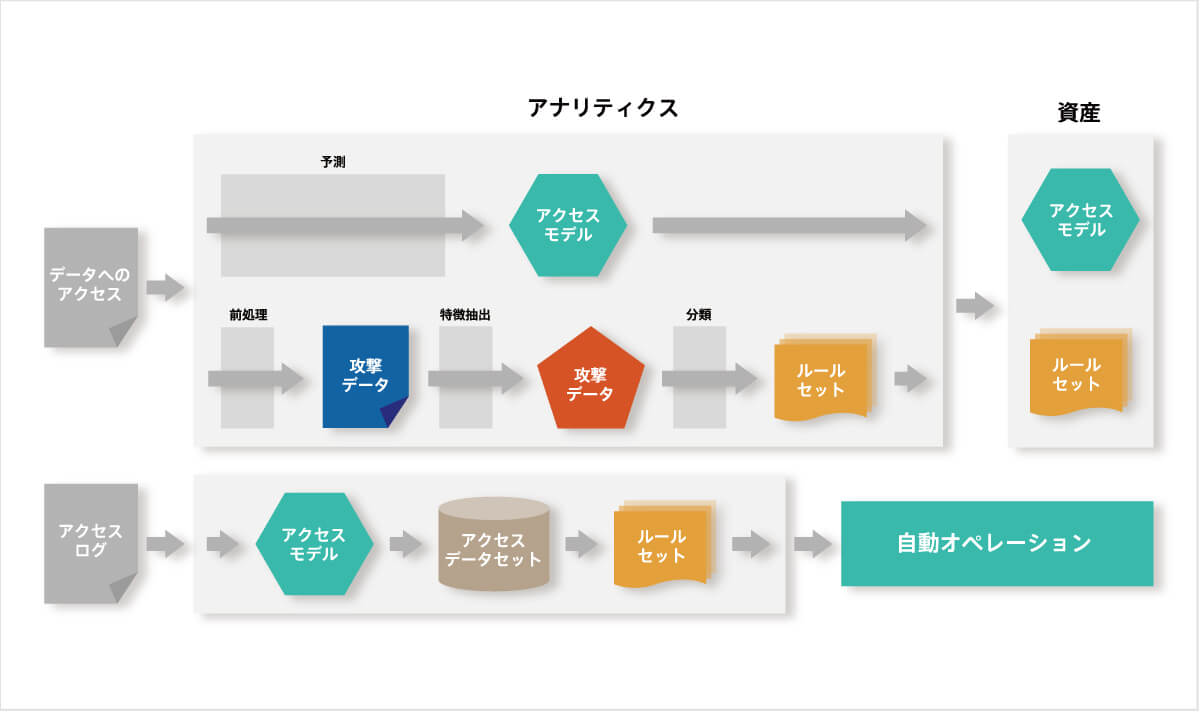
WEBサイトに対するルールの自動運用技術WRAOを開発し(特許取得済)、WAFのルール運用にかかるコストを縮小します。WRAOは、ユーザーのWebアクセスデータからWebサイトの通常時におけるアクセス傾向を学習するとともに、そのWebサイトへの攻撃特徴を予測します。これにより、モデル化されたWEBアプリケーションと攻撃モデルに適合した柔軟なルールの自動選択を可能にしました。
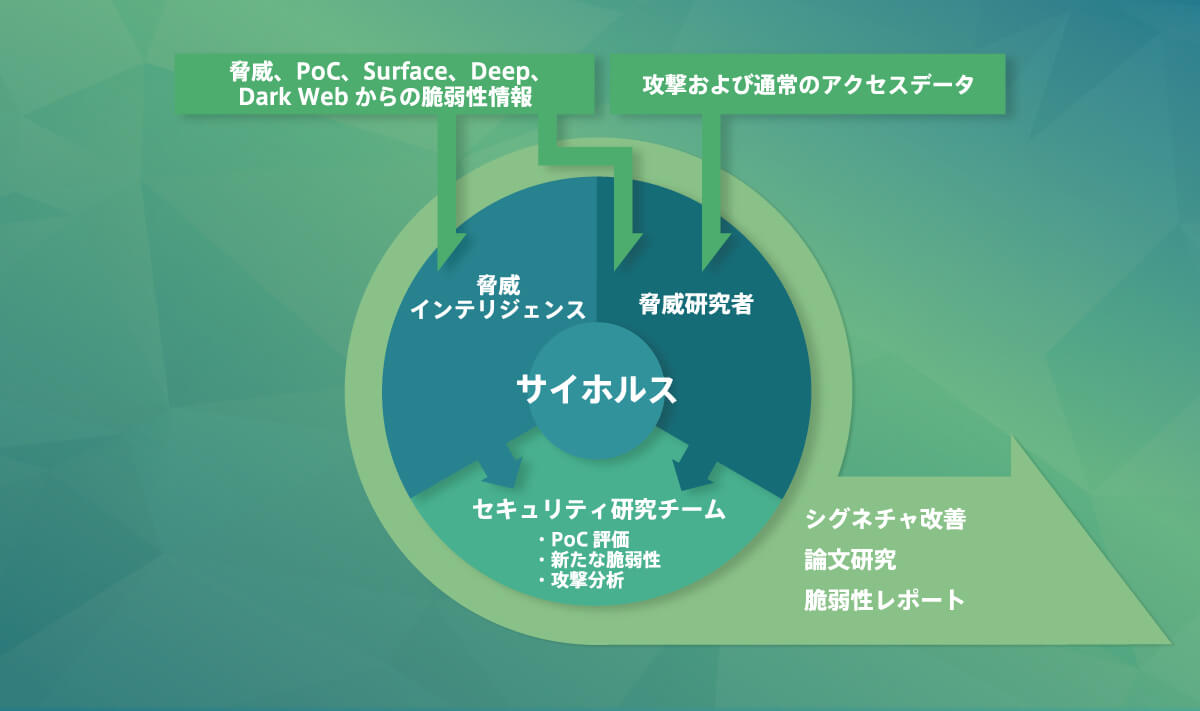
サイバー脅威情報の収集と評価、シグネチャへの反映スピードへの要求は日々高まるばかりです。Cyhorusは当社の精鋭によって組織されるチームであり、世界有数のサイバー脅威インテリジェンス情報を持つイスラエルの企業と提携、さらにインターネット上の情報や当社が持つ膨大な攻撃ログ等から本当に対応が必要な脅威を洗い出し正確な評価とシグネチャ作成まで一貫して行なっています。