News
- Press Release
[Survey report on the number of days from the occurrence of a cyber attack to its discovery and publication] Are many companies unaware? For corporations and organizations that have had more than 1,000 pieces of personal information leaked, it took more than a year from the time the cyberattack occurred until the attack was discovered!
Cyber Security Cloud, Inc. (Headquarters: Shinagawa-ku, Tokyo, Representative Director, President and CEO: Toshihiro Koike, hereinafter referred to as the "Company"), a global security manufacturer that provides anti-hacker services, will operate from January 1, 2022 to November 2023. We have published an investigation report (hereinafter referred to as the "Investigation") regarding the period from the occurrence of cyberattacks to their discovery and publication, based on personal information leakage cases related to unauthorized access that have been announced up to the 30th (more than 1,000 cases of personal information leakage). Masu.
■Although the period from attack detection to public announcement is somewhat shorter, the period from attack occurrence to attack detection remains unnoticed for nearly a year.
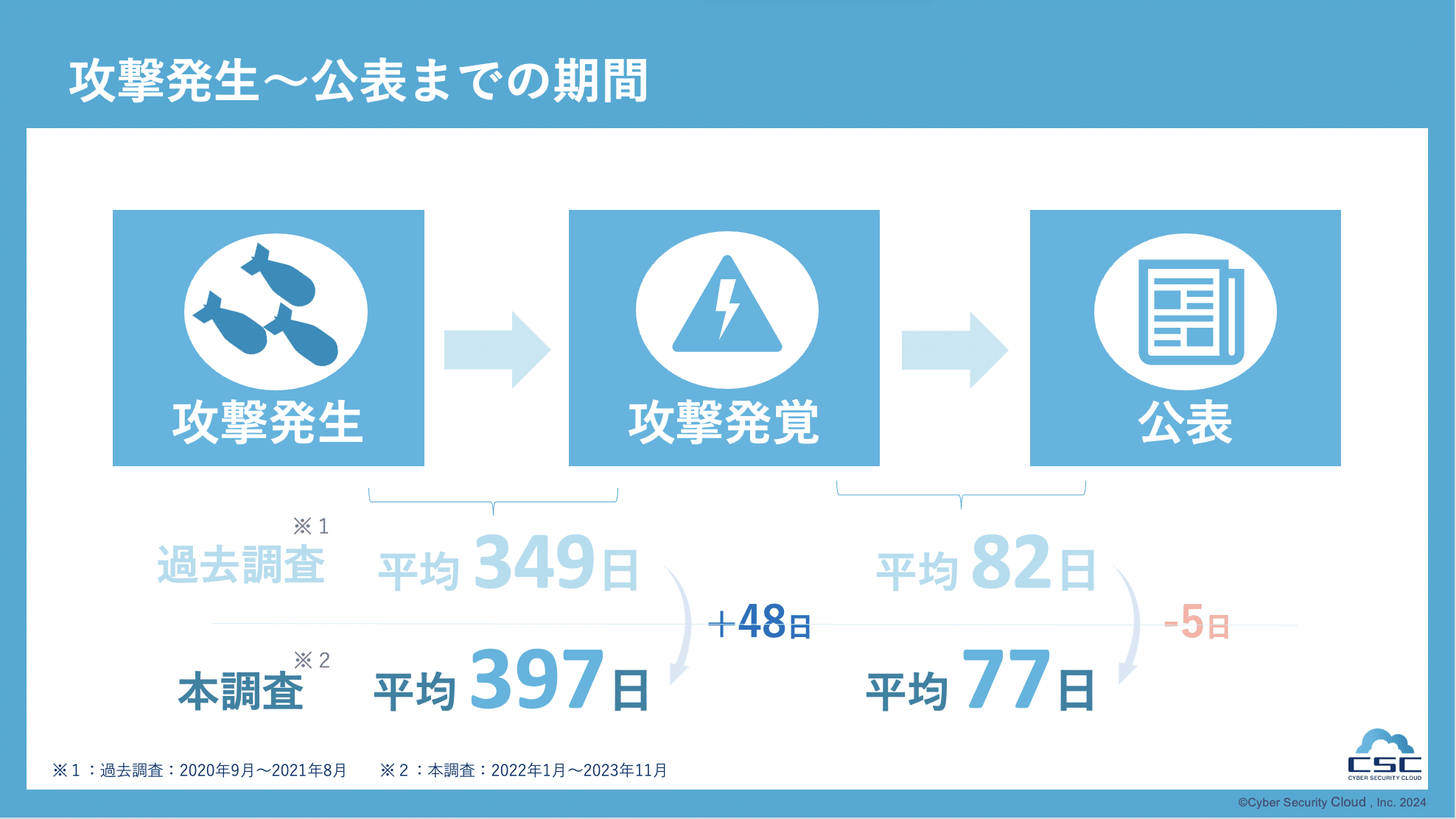
This survey found that it takes an average of 397 days from the time a company or organization receives a cyber attack to the time the attack is discovered. This is 48 days compared to the average number of days from "attack occurrence" to "attack detection" in surveys conducted by our company in the past (covering period from September 2020 to August 2021) (hereinafter referred to as "past surveys"). The days are getting longer.
Additionally, in this survey, it took an average of 77 days from the time the attack was discovered to the time the damage was made public, which is 5 days shorter than previous surveys.
As a result, there was a long period of time between the occurrence of an attack and the discovery of the attack, and it was found that the damage caused by a cyber attack was not noticed for more than a year. Additionally, although the time it took from ``discovery of an attack'' to ``publication'' was somewhat shortened, it was found that it still took more than two months to ``publicize'' the attack.
■ Approximately 40% of cases took more than a year from “attack occurrence” to “attack detection”, an increase of 11.4% from past surveys
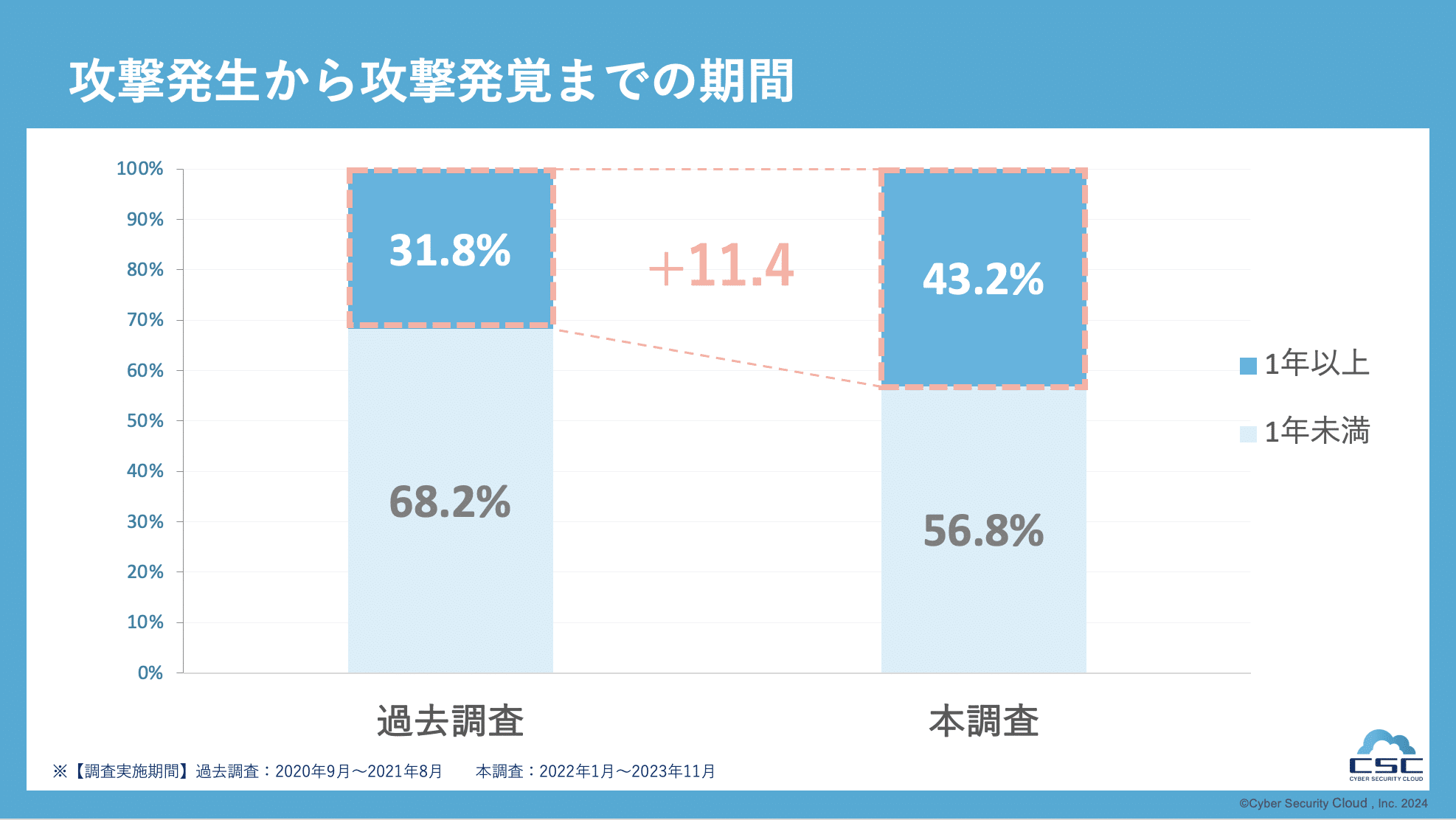
When classifying the period from the attack occurrence to the attack detection into ``less than a year'' and ``more than a year,'' 56.8% of the respondents answered ``less than a year.'' On the other hand, 43.2% of respondents answered "more than 1 year", an 11.4% increase from the previous survey. One of the reasons why it took more than a year for the attack to be discovered is that the attack exploited an unknown vulnerability (Zero-Day) and was not detected until the vulnerability became publicly known. Furthermore, as web applications are constantly changing, with new features and updates occurring frequently, vulnerabilities can remain unaddressed for long periods of time due to issues such as the resources and costs required to update and monitor web applications. .
■57% of cases took more than a month from “attack discovery” to “publication”
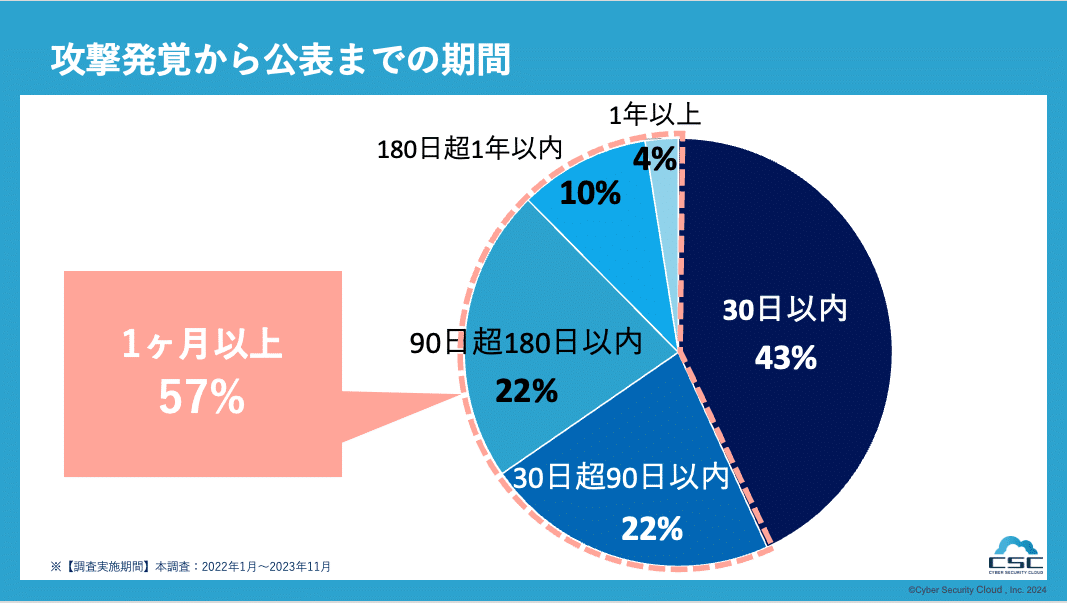
As a result of classifying the period from ``attack discovery'' to ``announcement,'' 57% of cases took more than a month. There are multiple factors behind this prolonged period. While it is necessary to identify the cause of the damage and the extent of the impact, and provide appropriate notification and explanation to affected stakeholders before making a public announcement, companies may not have enough human resources, or there may be a lack of clarity regarding the process from attack discovery to publication. It is believed that the time until publication is taking a long time due to various factors, including the lack of regulations.
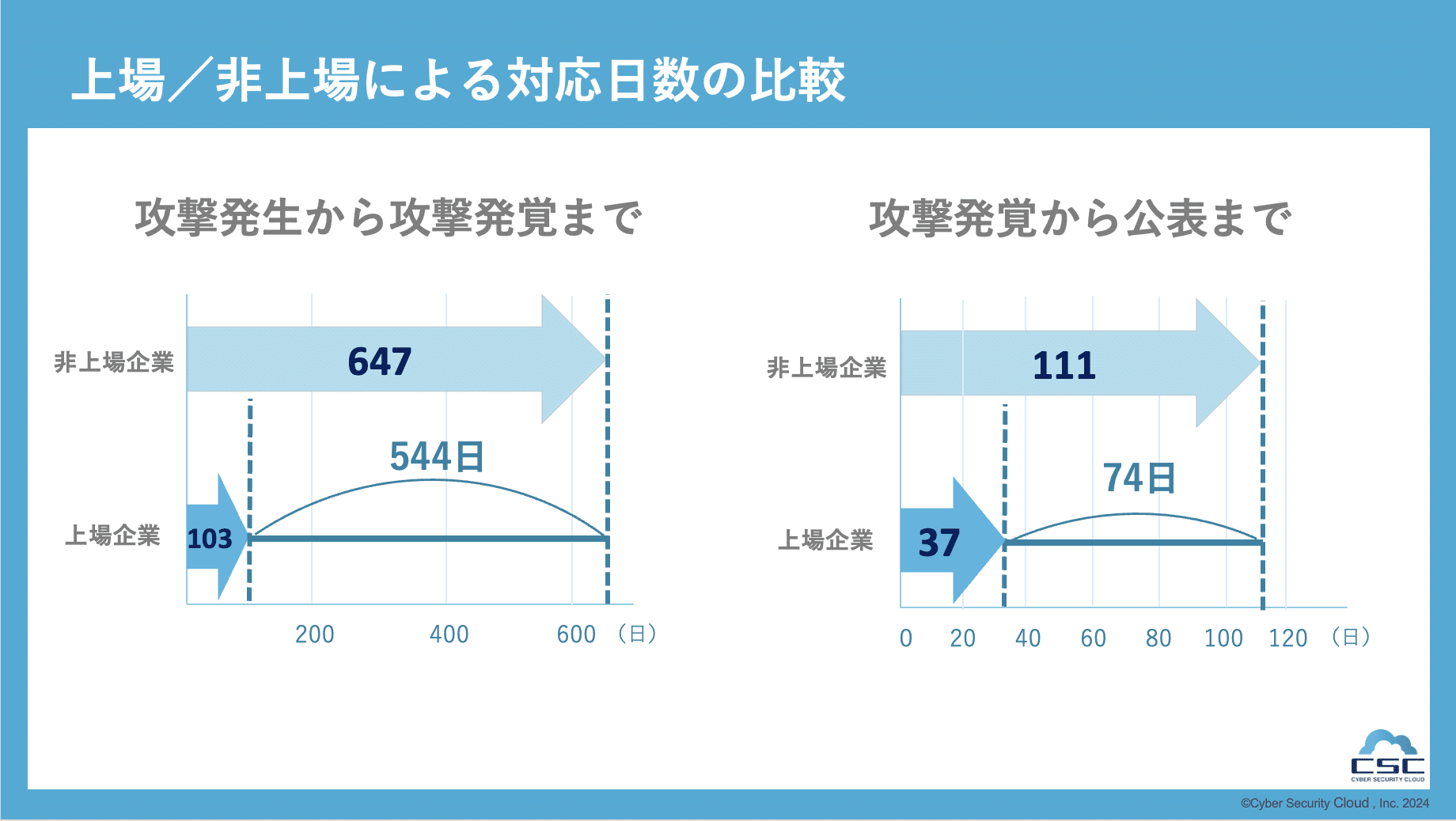
When comparing the time required from the occurrence of an attack to the detection of an attack between listed and unlisted companies, the average time for listed companies was 103 days, while for unlisted companies it was 647 days. Additionally, the time it took from ``detection of an attack'' to ``publication'' was 37 days for listed companies, but 111 days for unlisted companies. It can be seen that listed companies respond faster to cyber-attacks than non-listed companies. One of the reasons for this difference is that listed companies are required to focus on compliance and the impact on stakeholders, and to respond quickly.
■Comment from Yoji Watanabe Representative Director, CTO Cyber Security Cloud
In this study, the average period from when an attack occurred until it was discovered was 397 days. This allows attackers to remain in systems for extended periods of time and maintain access to valuable corporate data. This situation is especially noticeable among small and medium-sized enterprises. Small and medium-sized businesses with a shortage of cybersecurity talent and limited resources need more time to discover and respond to attacks. On the other hand, the fact that the period from ``attack detection'' to ``publication'' has become somewhat shorter suggests that security awareness and response speed have improved. In particular, listed companies tend to be more aware of cybersecurity and respond more quickly than non-listed companies. However, the reason why it takes more than two months to make a public announcement is due to a detailed investigation to confirm what kind of data was leaked and what systems were accessed by the attackers. It may take time to perform analysis and gather accurate information. Additionally, in many cases, the details of a cyberattack are not made public and are only discovered years later.
Cybersecurity is an essential element for businesses. Given these findings, companies should continue to strengthen their cybersecurity posture through the latest technology and continued education.
<Investigation overview>
-Survey period: January 1, 2022 to November 30, 2023
-Survey target: Major personal information leakage cases involving unauthorized access to corporations and organizations that were announced by the above period (92 cases) with damage scale of 1,000 or more
-Research method: Cyber Security Cloud research
■ About Cyber Security Cloud, Inc.
Address: JR Tokyu Meguro Building 13F, 3-1-1 Kamiosaki, Shinagawa-ku, Tokyo
Representative: Toshihiro Koike Representative Director, President and CEO
Established: August 2010
URL: https://www.cscloud.co.jp
Cyber Security Cloud has a management philosophy of "creating a safe and secure cyber space for people around the world", and utilizes world-class cyber threat intelligence and AI technology to provide web application security services and vulnerability information collection.・We provide anti-hacker services such as management tools. We will continue to contribute to the promotion of the information revolution as one of the leading global companies in cyber security, with a focus on WAF.
