News
- Press Release
Number of detections increased 50-fold overnight, large-scale attack spike occurred in late July. "Web Application Cyber Attack Detection Report for July-September 2025" released.
Cyber Security Cloud, Inc. (Headquarters: Shinagawa-ku, Tokyo; Representative Director, President and CEO: Toshihiro Koike; hereinafter referred to as "Cyber Security Cloud"), a global security manufacturer, is pleased to announce the release of its "Web Application Cyber Attack Detection Report" (hereinafter referred to as "this Report"), covering the period from July 1 to September 30, 2025. This Report aggregates, analyzes, and calculates cyber attack logs observed by Cyber Security Cloud's Cloud-based WAF "Shadankun," which visualizes and blocks cyber attacks on web applications, and its public cloud WAF automated operation service "WafCharm."
<Report Summary>
・More than 500 million attacks detected in the three months from July to September 2025
Attacks targeting cloud connection routes increased approximately 13.6 times compared to the previous year
・A large-scale spike in attacks was observed in late July, with the number of detections increasing by up to 50 times compared to normal levels
■ Overall Overview: Over 500 million attacks detected
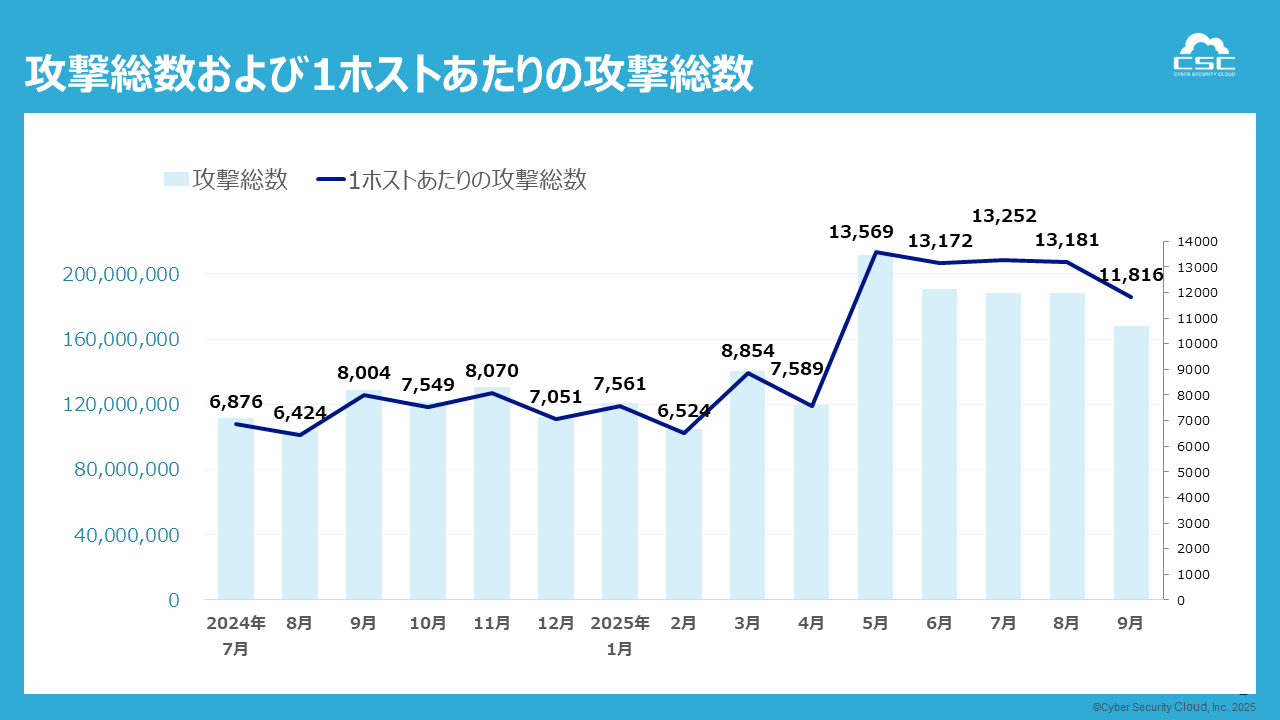
The total number of attacks detected between July and September 2025 was approximately 544 million.
Looking at monthly trends, the number of attacks has remained at a high level since before July, and although it decreased slightly in September, a large number of attacks have continued to be observed.
Furthermore, the number of attacks per host*1 has increased by approximately 2 times compared to the previous year.
*1 Estimated using the total number of hosts protected by "Shadankun" (Web type: number of FQDNs, Server type: number of IPs) and the total number of hosts protected by "WafCharm" (WebACLs) as the denominator.
■ Attack type composition and trends
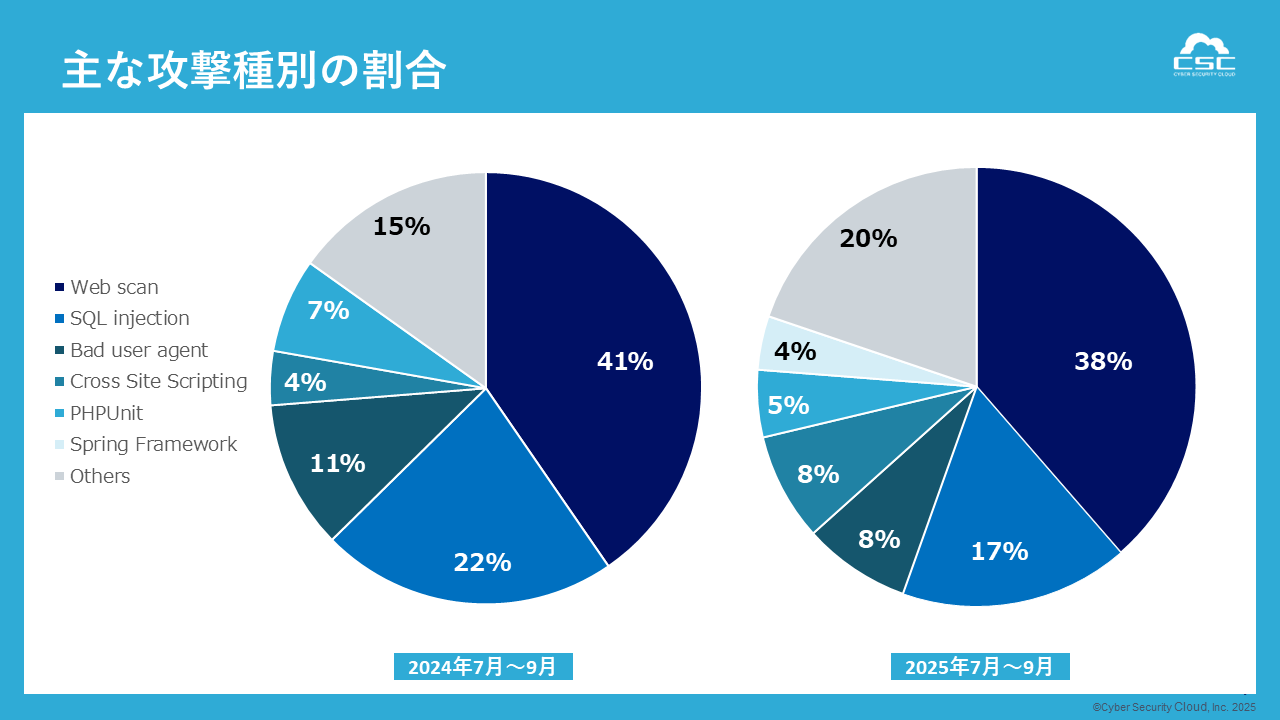
Looking at the trends in the main types of attacks during this survey period, the total number of attacks increased, but there was no significant change in the composition of attack types.
This report shows that traditional web application attacks, such as SQL injection (SQLi) and cross-site scripting (XSS), continue to be observed frequently. While these attack methods have remained major threats for many years, in recent years attacks have become increasingly automated and large-scale, with the number of detected attacks reaching record highs. In particular, web applications with insufficient input validation and configuration issues such as misconfigurations and inadequate access control pose a risk of security holes and could serve as a foothold for attacks.
■ Attacks targeting cloud connection routes increased approximately 13.6 times compared to the previous year
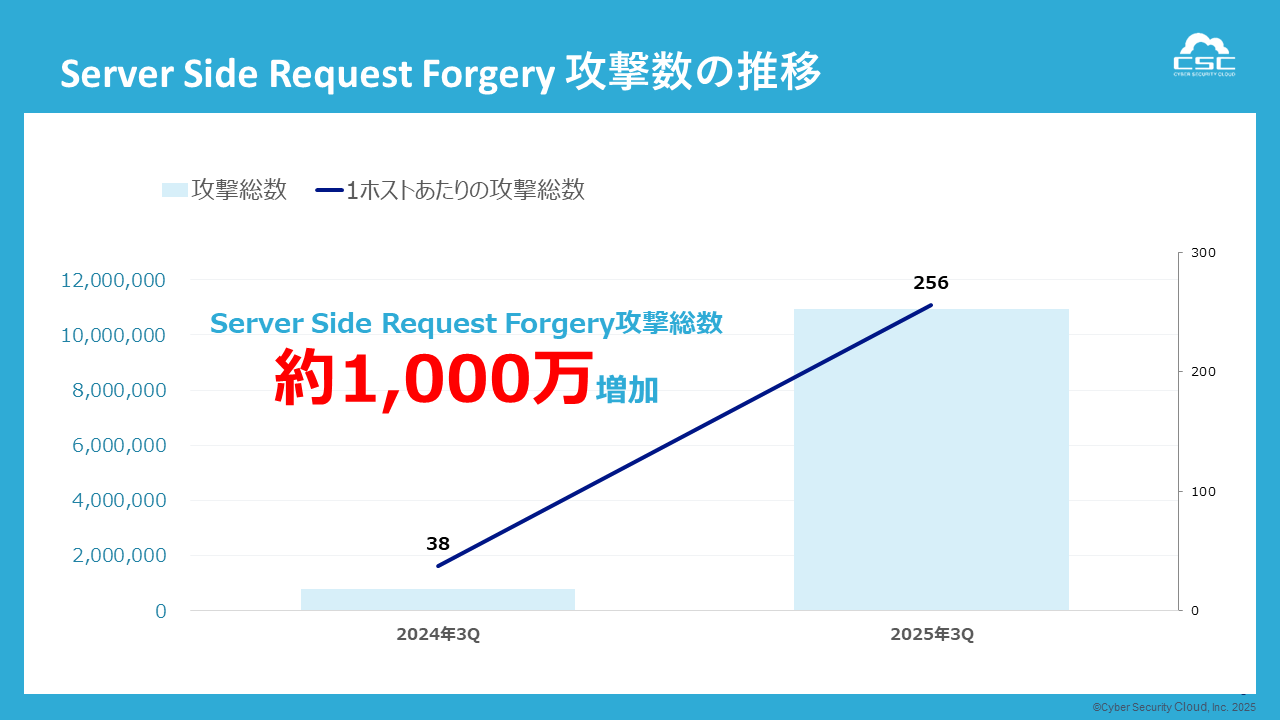
The number of Server Side Request Forgery (SSRF) detections observed in the third quarter of 2025 (July to September) was approximately 10.94 million, a sharp increase of approximately 13.6 times from the same period last year (3rd quarter of 2024: 800,000 cases).
This type of attack uses malicious input when an application makes an external request, leading to unauthorized access to internal servers or cloud metadata services.With the spread of cloud computing and microservices, the attack surface is rapidly expanding.
There was a significant increase in SSRF-related traffic from late July to early September. The sources were distributed across multiple countries, and the attacks exhibited characteristics of automated botnet scans and information gathering attacks exploiting API routes. The increase in SSRF was also linked to an overall increase in web attacks, and it was confirmed that attack groups targeting the API layer and data exchange layer were becoming more active, similar to traversal attacks and XML External Entity (XXE) attacks.
The background to this trend is the increasing complexity of service integration in cloud environments and the exposure of internal APIs and metadata endpoints in development sites. There are increasing cases where minor configuration flaws, such as misconfigurations or relaxed permissions, are exploited as attack vectors.
For example, if an SSRF attack is successful in a cloud environment, an attacker may be able to access the metadata API within the cloud environment to obtain authentication information or perform lateral movement via the internal network. As a result, there is an increased risk of serious damage, such as service account hijacking and confidential data leakage.
■ Trends in attack sources
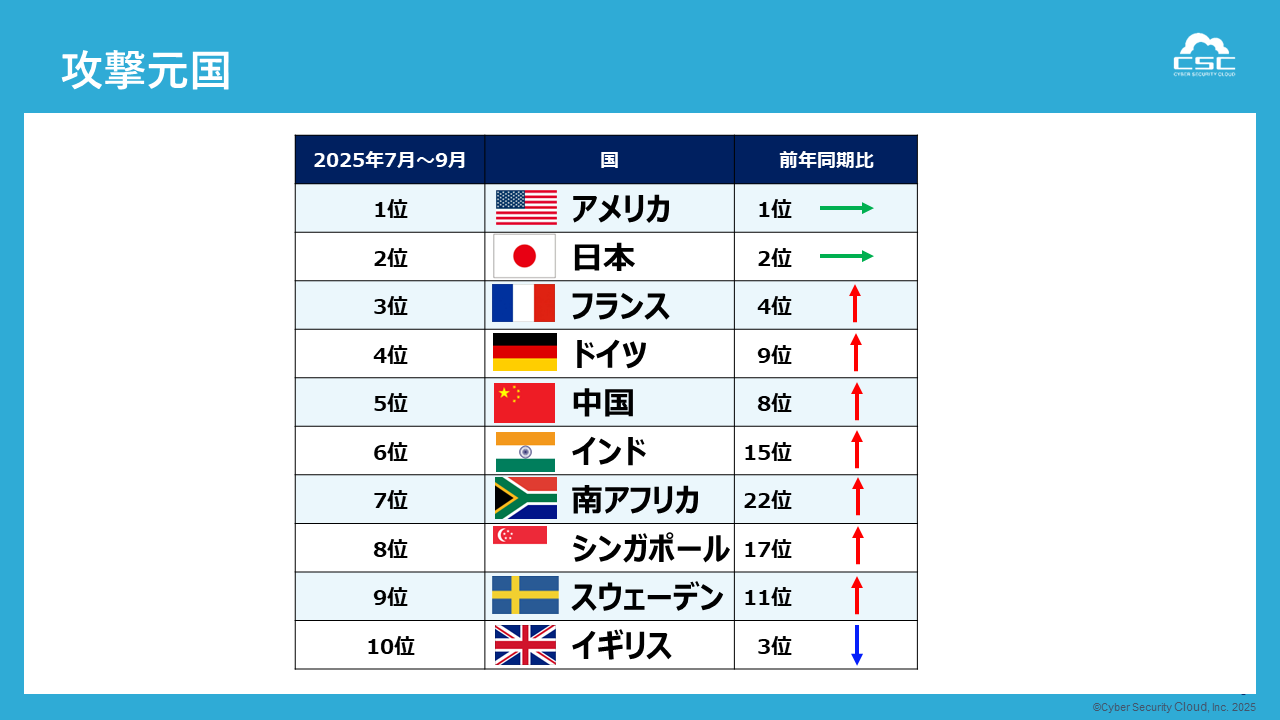
When the source IP addresses of the attacks were classified by country, the United States was the most prevalent, accounting for approximately half of the total. Japan, France, Germany, and China followed in that order, demonstrating the continuing tripolar structure of North America, Europe, and Asia.
■ Anomaly detection analysis
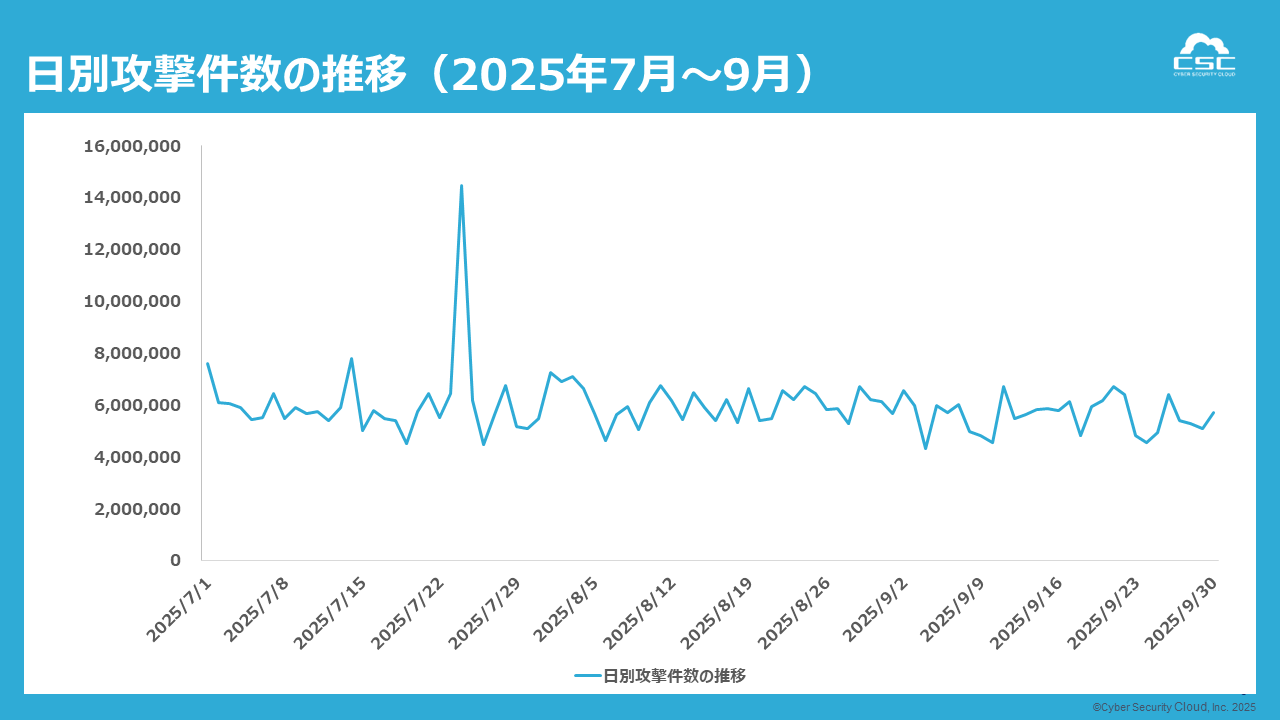
In late July 2025, a significant increase in attacks was observed.
During this period, multiple attack methods, including SQL injection and cross-site scripting (XSS), occurred simultaneously, suggesting the possibility that an automated attack campaign was being carried out.
In particular, from July 23rd to 24th, multiple attack rules recorded detection numbers that were tens to hundreds of times higher than normal.
These attacks are not targeted at any specific company or system, but are believed to be indiscriminate, large-scale scanning attacks carried out worldwide. Analysis of the attacks revealed a notable attempt to search for vulnerable applications through web forms and URL parameters.
Additionally, many of the requests used in the attack had URL structures with automatically generated strings and sequential numbers, suggesting that they were sent en masse by bots or scripts rather than manually.
Furthermore, even after the July surge, waves of smaller attacks occurred intermittently from August to September, suggesting that these were not one-off attempts but rather long-term, exploratory attack activities. In particular, with regard to SQL injection, there were repeated attempts to identify internal system information and database structures.
Such attacks could potentially affect services used by many companies, such as cloud environments and public APIs, so it will become increasingly important to strengthen monitoring systems that can quickly detect and block abnormal concentrations of requests.
■Comment from Yoji Watanabe Representative Director, CTO Cyber Security Cloud, Inc.
Attacks targeting the web application layer continued to be observed both domestically and internationally in the third quarter of 2025. In particular, the sharp increase in Server Side Request Forgery (SSRF) attacks targeting cloud connection routes is symbolic, indicating that development environments such as clouds and APIs are attracting attention as new targets for attacks.
Additionally, in late July, multiple conventional attack methods such as SQL injection and XSS were observed simultaneously, revealing that automated scanning attacks were being carried out on a global scale. This is not a passing phenomenon, but suggests that attackers are now making full use of AI and automation tools to combine a variety of methods in a shorter period of time.
As attacks continue to evolve, defenses must also become more automated and sophisticated. We will continue to support businesses in creating an environment where they can "use the cloud safely and securely" by optimizing detection rules in real time in our WAF products and strengthening defense automation in accordance with cloud configurations.
Cyberattacks are no longer an industry-specific issue, but a societal challenge common to all digital services. We will continue to lead the way in promoting a culture in which security is considered a "prerequisite from the design stage" rather than an "add-on."
About Cyber Security Cloud, Inc.
Company name: Cyber Security Cloud, Inc.
Address: 13F JR Tokyu Meguro Building, 3-1-1 Kami-Osaki, Shinagawa-ku, Tokyo 141-0021
Representative: Toshihiro Koike Representative Director, President and CEO
Established: August 2010
URL: https://www.cscloud.co.jp
With the mission of "creating a cyberspace that people all over the world can use safely and securely," we are a Japanese security manufacturer that provides vulnerability information collection and management tools and fully managed security services for cloud environments, centered on web application security services that make full use of the world's leading cyber threat intelligence. As one of the global companies in cybersecurity, we will contribute to solving social issues related to cybersecurity and provide added value to society.
